Bandit Level 0 → 1
The password for the next level is stored in a file called readme located in the home directory. Use this password to log into bandit1 using SSH. Whenever you find a password for a level, use SSH (on port 2220) to log into that level and continue the game
Solution
The level 0 requires us to login wargame via ssh.
1
ssh username@host [-p port]
Back to wargame, I will use https://bandit.labs.overthewire.org/ is the host, on port 2220, with both username and password are bandit0. Open SSH, and login!
1
ssh bandit0@bandit.labs.overthewire.org -p 2220
All I need to do is read it!
1
2
bandit0@bandit:~$ cat readme
NH2SXQwcBdpmTEzi3bvBHMM9H66vVXjL
Flag: NH2SXQwcBdpmTEzi3bvBHMM9H66vVXjL
Bandit Level 1 → 2
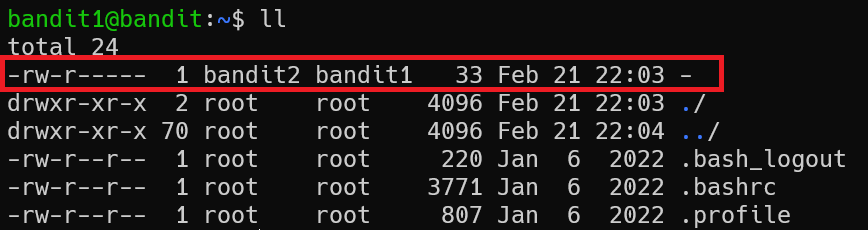
The password for the next level is stored in a file called - located in the home directory
Solution
1
ssh bandit1@bandit.labs.overthewire.org -p 2220
There are several ways to read dashed filename. Simply I just use cat ./-. Additionally, you can use cat < -
1
2
bandit1@bandit:~$ cat ./-
rRGizSaX8Mk1RTb1CNQoXTcYZWU6lgzi
Flag: rRGizSaX8Mk1RTb1CNQoXTcYZWU6lgzi
Bandit Level 2 → 3
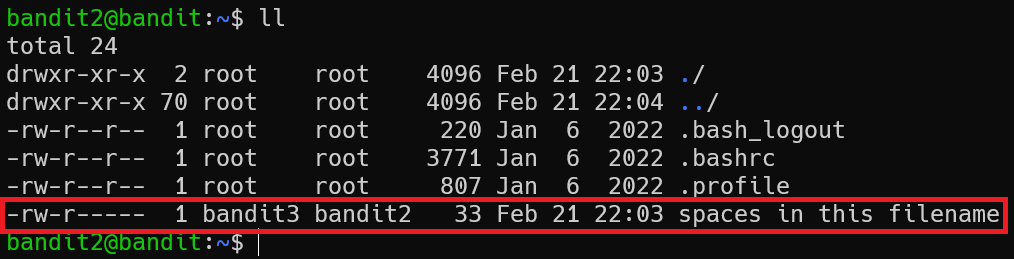
The password for the next level is stored in a file called spaces in this filename located in the home directory
Solution
There’s the password file, just read it and move on. But… Let’s take a closer look at file name. If you use cat spaces in this filename, cat thinks we want to read 4 files. So, in this case, I can put filename to '' or put \ before spaces character
1
2
3
cat 'spaces in this filename'
or
cat spaces\ in\ this\ filename
Result:
1
2
bandit2@bandit:~$ cat spaces\ in\ this\ filename
aBZ0W5EmUfAf7kHTQeOwd8bauFJ2lAiG
Flag: aBZ0W5EmUfAf7kHTQeOwd8bauFJ2lAiG
Bandit Level 3 → 4
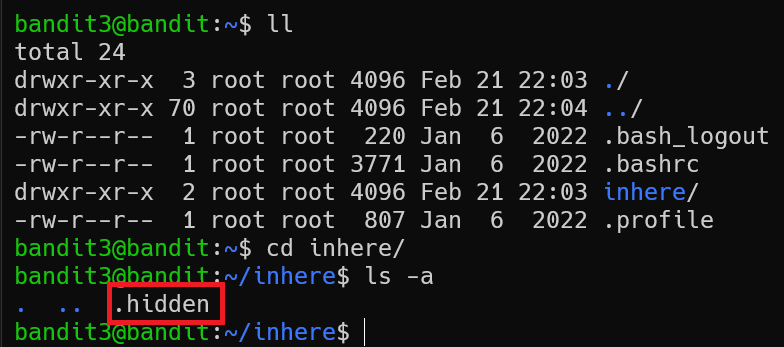
The password for the next level is stored in a hidden file in the inhere directory.
Solution
There’s a inhere directory in bandit3’s home dir.
Use ls -a to list all content in a directory, consist of hidden files.
Let’s cat it and move on!
1
2
bandit3@bandit:~/inhere$ cat .hidden
2EW7BBsr6aMMoJ2HjW067dm8EgX26xNe
Flag: 2EW7BBsr6aMMoJ2HjW067dm8EgX26xNe
Bandit Level 4 → 5
The password for the next level is stored in the only human-readable file in the inhere directory.
Tip: if your terminal is messed up, try the “reset” command.
Solution
There’s inhere directory, let’s see the content of this.
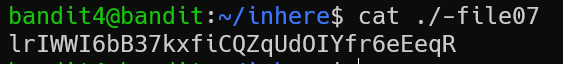
Here you can see multiple of dash filename that already learnt in level 1. According to the challenge, the password’s stored in the only HUMAN-READABLE file (ascii text format).
1
find . -exec file {} + | grep ASCII
Flag: lrIWWI6bB37kxfiCQZqUdOIYfr6eEeqR
Bandit Level 5 → 6
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
Solution
I make use of find command. Learn more find command here
1
2
bandit5@bandit:~/inhere$ find . ! -executable -size 1033c -exec file {} + | grep ASCII
./maybehere07/.file2: ASCII text, with very long lines (1000)
This means I find in current directory, a non-executable file with -size is 1033c (c for bytes), read more at man find.
1
2
bandit5@bandit:~/inhere$ cat ./maybehere07/.file2
P4L4vucdmLnm8I7Vl7jG1ApGSfjYKqJU
Flag: P4L4vucdmLnm8I7Vl7jG1ApGSfjYKqJU
Bandit Level 6 → 7
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
Solution
Seem likes it’s similar to the previous level. Keyword is “somewhere on the server” So I’ll look on entire filesystem instead of finding in current directory.
1
2
bandit6@bandit:~$ find / -user bandit7 -group bandit6 -size 33c 2>/dev/null
/var/lib/dpkg/info/bandit7.password
I used 2> /dev/null what for? 2 refers to stderr (standard error). This means all of the error message in this output will be redirected to /dev/null, which is a null device file. This will discard anything written to it, and will return EOF on reading.
1
2
bandit6@bandit:~$ cat /var/lib/dpkg/info/bandit7.password
z7WtoNQU2XfjmMtWA8u5rN4vzqu4v99S
Flag: z7WtoNQU2XfjmMtWA8u5rN4vzqu4v99S
Bandit Level 7 → 8
The password for the next level is stored in the file data.txt next to the word millionth
Solution
There’s a data.txt file in home directory, just grep millionth in it to find the password.
1
2
bandit7@bandit:~$ grep 'millionth' data.txt
millionth TESKZC0XvTetK0S9xNwm25STk5iWrBvP
Flag: TESKZC0XvTetK0S9xNwm25STk5iWrBvP
Bandit Level 8 → 9
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
Solution
This challenge require us to know how to filter one line different from the others using some necessary command like sort, uniq
1
2
bandit8@bandit:~$ sort data.txt | uniq -u
EN632PlfYiZbn3PhVK3XOGSlNInNE00t
Where, sort then sorts the output alphabetically
uniq -u show the unique lines , but it only works on ordered lists, so I’ve to sort first.
Flag: EN632PlfYiZbn3PhVK3XOGSlNInNE00t
Bandit Level 9 → 10
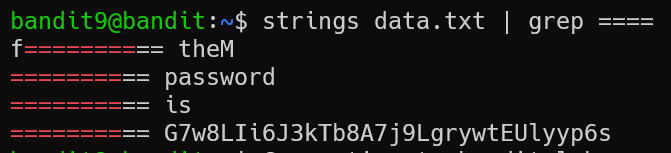
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
Solution
Just strings file data.txt to meet with the human-readable characteristic and grep several ‘=’ character to find the password
Flag: G7w8LIi6J3kTb8A7j9LgrywtEUlyyp6s
Bandit Level 10 → 11
The password for the next level is stored in the file data.txt, which contains base64 encoded data
Solution
Read file data.txt, then I get a base64 encoded data. I solved it by using base64 from coreutils package to decode it. The syntax is:
1
base64 [option]… [file]
Read more about base64 in RFC4648
1
2
bandit10@bandit:~$ base64 --decode data.txt
The password is 6zPeziLdR2RKNdNYFNb6nVCKzphlXHBM
Flag: 6zPeziLdR2RKNdNYFNb6nVCKzphlXHBM
Bandit Level 11 → 12
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
Solution
See the content of data.txt
1
2
bandit11@bandit:~$ cat data.txt
Gur cnffjbeq vf WIAOOSFzMjXXBC0KoSKBbJ8puQm5lIEi
Combined with challenge’s description, the data have been rotated by 13 position => rot13
For that, I use tr command, completed syntax is:
1
tr '[a-zA-Z]' '[n-za-mN-ZA-M]'
Explanation: Every “A” is replaced by an “N”, every “B” by an “O”, so on.
1
2
bandit11@bandit:~$ cat data.txt | tr '[a-zA-Z]' '[n-za-mN-ZA-M]'
The password is JVNBBFSmZwKKOP0XbFXOoW8chDz5yVRv
Flag: JVNBBFSmZwKKOP0XbFXOoW8chDz5yVRv
Bandit Level 12 → 13
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
Solution
First, I’ll open data.txt file in home dir and check it!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
bandit12@bandit:~$ cat data.txt
00000000: 1f8b 0808 8c3f f563 0203 6461 7461 322e .....?.c..data2.
00000010: 6269 6e00 0134 02cb fd42 5a68 3931 4159 bin..4...BZh91AY
00000020: 2653 5953 6696 8100 001b 7fff fbdb effb &SYSf...........
00000030: b41f 6efa a7cb ebee fff3 b7ad 897d f77f ..n..........}..
00000040: 67bf beff bb6b aaff ff3b ff7b b001 3b5b g....k...;.{..;[
00000050: 4100 00d0 3101 881a 0d34 01a0 000d 0006 A...1....4......
00000060: 10c4 d006 41b5 1a0d 0064 0340 64c8 3468 ....A....d.@d.4h
00000070: 1934 1a0d 1a68 da26 26d3 50e4 d0d3 40d0 .4...h.&&.P...@.
00000080: d001 a341 b500 0032 320d 0323 47a9 a683 ...A...22..#G...
00000090: 4346 9a00 3d40 36a0 0308 184d 0640 0068 CF..=@6....M.@.h
000000a0: 0c43 466a 0d34 6832 9a68 6430 40d3 4d34 .CFj.4h2.hd0@.M4
000000b0: d0d0 7a80 d0c2 69a3 268d 1a06 81a0 00d0 ..z...i.&.......
000000c0: c83f 5232 3400 c406 8da8 0680 3400 6800 .?R24.......4.h.
000000d0: 001a 0020 2823 e282 2299 1ae9 cfa4 8ea0 ... (#..".......
000000e0: 716d 6e03 9844 dd8b 7260 8c1e e05c d068 qmn..D..r`...\.h
000000f0: 9a86 f4d8 b355 8786 1723 3041 695d f96a .....U...#0Ai].j
00000100: f8c0 503b 8df1 eac8 138b 82ed 21cb 9611 ..P;........!...
00000110: 6d6a e5c3 c7ca 637c 26d9 ed7e 107a 14a2 mj....c|&..~.z..
00000120: 6c54 8868 511f 481a 6412 bb95 a771 0401 lT.hQ.H.d....q..
00000130: 3ca4 96cf 7e08 0e31 d967 e4c4 4fee 206b <...~..1.g..O. k
00000140: 8793 ec23 4da7 44ba 3ded 12e2 b947 9288 ...#M.D.=....G..
00000150: 7809 0ca2 6b04 5f0d e0b2 6717 7e87 0628 x...k._...g.~..(
00000160: 11a3 d282 9d61 f0a4 340c af19 d501 4ddd .....a..4.....M.
00000170: 1a8c c27b 154c 531f 345c b6a2 7298 a20c ...{.LS.4\..r...
00000180: e02d bb16 9127 5b42 30d6 634c b7cd 54ae .-...'[B0.cL..T.
00000190: bb26 9494 2a19 33bc b233 0d8c a75a ccf8 .&..*.3..3...Z..
000001a0: 401c d5f4 bd06 7c43 cd73 32d3 84d0 c440 @.....|C.s2....@
000001b0: 004e b2e9 de84 8251 e080 1a1e f506 e546 .N.....Q.......F
000001c0: cf30 31af 361e b04c 8f5a f636 f1e7 4c24 .01.6..L.Z.6..L$
000001d0: e14b 456b 109e 1421 99e5 ead9 3840 038f .KEk...!....8@..
000001e0: c1d8 c71a 9b5d 5435 afa0 5eca 34ca a83c .....]T5..^.4..<
000001f0: 309e 6b5d 532f a0af 20e0 bc3f bb03 a680 0.k]S/.. ..?....
00000200: 6616 4b13 9d09 bf8b 3a93 6f16 b48a e6cf f.K.....:.o.....
00000210: ccb9 084c 8a35 12a7 447d 8224 4491 e534 ...L.5..D}.$D..4
00000220: 0c71 2f36 fda1 8b54 0808 a144 9894 966f .q/6...T...D...o
00000230: be74 2140 952c 0294 a1d6 841e 1658 756f .t!@.,.......Xuo
00000240: 0d7f c5dc 914e 1424 14d9 a5a0 4043 a8c0 .....N.$....@C..
00000250: f434 0200 00 .4...
Here as you can see, it’s a hexdump which is made by xxd command and reversed also by it
Referring to challenge’s description, Let’s create a directory in tmp file and make edits on data.txt file
1
2
3
4
5
6
bandit12@bandit:~$ mktemp -d
/tmp/tmp.UXHp76B0fO
bandit12@bandit:~$ cp data.txt /tmp/tmp.UXHp76B0fO
bandit12@bandit:~$ cd /tmp/tmp.UXHp76B0fO
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ ls
data.txt
Now, we have to reverse hexdump using xxd
1
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ xxd -r data.txt > password
-r option for running the reverse hexdump, and > redirect to password file. Then, we should check what type of password file:
1
2
3
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file password
password: gzip compressed data, was "data2.bin", last modified: Tue Feb 21 22:02:52 2023, max compression, from Unix, original size modulo 2^32 564
From here on, the flow as below steps:
- Using
filecommand to determine the type of file - Using
mvcommand to change the file type to specific file extension. - Using the appropriate unzip tools to decompress files (gzip/gunzip, bzip2, tar,…)
- Repeat and repeat to get the password!
And, the summarized result is here:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ xxd -r data.txt > password
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file password
password: gzip compressed data, was "data2.bin", last modified: Tue Feb 21 22:02:52 2023, max compression, from Unix, original size modulo 2^32 564
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv password password.gz
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ gunzip password.gz
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file password
password: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv password password.bz2
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ bzip2 -d password.bz2
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file password
password: gzip compressed data, was "data4.bin", last modified: Tue Feb 21 22:02:52 2023, max compression, from Unix, original size modulo 2^32 20480
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv password password.gz
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ gunzip password.gz
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file password
password: POSIX tar archive (GNU)
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv password password.tar
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ tar -xvf password.tar
data5.bin
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file data5.bin
data5.bin: POSIX tar archive (GNU)
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv data5.bin data5.tar
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ tar -xvf data5.tar
data6.bin
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file data6.bin
data6.bin: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv data6.bin data6.bz2
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ bzip2 -d data6.bz2
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file data6
data6: POSIX tar archive (GNU)
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv data6 data6.tar
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ tar -xvf data6.tar
data8.bin
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file data8.bin
data8.bin: gzip compressed data, was "data9.bin", last modified: Tue Feb 21 22:02:52 2023, max compression, from Unix, original size modulo 2^32 49
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ mv data8.bin data8.gz
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ gunzip data8.gz
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ file data8
data8: ASCII text
bandit12@bandit:/tmp/tmp.UXHp76B0fO$ cat data8
The password is wbWdlBxEir4CaE8LaPhauuOo6pwRmrDw
Flag: wbWdlBxEir4CaE8LaPhauuOo6pwRmrDw
Bandit Level 13 → 14
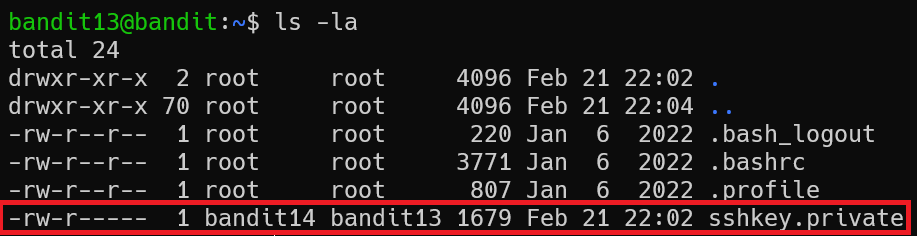
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
Solution
This challenge require us to know about SSH and SSH Key. If you haven’t known about it yet, you can read it here
Try login the bandit14’s box using SSH Key in home directory’s bandit13 with the provided information.
1
bandit13@bandit:~$ ssh -i "sshkey.private" bandit14@localhost -p 2220
Boom! I’ve just entered the bandit14’s box! Let’s get the password in the /etc/bandit_pass/bandit14:
1
2
bandit14@bandit:~$ cat /etc/bandit_pass/bandit14
fGrHPx402xGC7U7rXKDaxiWFTOiF0ENq
Flag: fGrHPx402xGC7U7rXKDaxiWFTOiF0ENq
Bandit Level 14 → 15
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
Solution
The solution here we can use either nc or telnet. This means, we submit the current password’s bandit14 (you can retrieve in the /etc/bandit_pass/bandit14) to localhost port 30000.
1
2
3
4
bandit14@bandit:~$ nc localhost 30000
fGrHPx402xGC7U7rXKDaxiWFTOiF0ENq
Correct!
jN2kgmIXJ6fShzhT2avhotn4Zcka6tnt
Additionally, we can use echo fGrHPx402xGC7U7rXKDaxiWFTOiF0ENq | nc localhost 30000 . When we run this command, we take the STDOUT of echo and pipe it as the STDIN of netcat. It returns the same result.
Or we can use telnet instead.
1
2
3
4
5
6
7
8
9
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
fGrHPx402xGC7U7rXKDaxiWFTOiF0ENq
Correct!
jN2kgmIXJ6fShzhT2avhotn4Zcka6tnt
Connection closed by foreign host.
Flag: jN2kgmIXJ6fShzhT2avhotn4Zcka6tnt
Bandit Level 15 → 16
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
Helpful note: Getting “HEARTBEATING” and “Read R BLOCK”? Use -ign_eof and read the “CONNECTED COMMANDS” section in the manpage. Next to ‘R’ and ‘Q’, the ‘B’ command also works in this version of that command…
Helpful Reading Material
Solution
Read the hint, as we can see, the level goal mentions ssl, there’s a tool called openssl. Let’s look there:
1
2
3
4
5
6
7
8
9
s_client
This implements a generic SSL/TLS client which can establish a
transparent connection to a remote server speaking SSL/TLS. It's
intended for testing purposes only and provides only rudimentary
interface functionality but internally uses mostly all
functionality of the OpenSSL ssl library.
-connect
Tests connectivity to an HTTPS service.
Let’s connect to the given port via openssl as above options.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
bandit15@bandit:~$ openssl s_client -connect localhost:30001
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 CN = localhost
verify error:num=18:self-signed certificate
verify return:1
depth=0 CN = localhost
verify error:num=10:certificate has expired
notAfter=Mar 4 13:56:53 2023 GMT
verify return:1
depth=0 CN = localhost
notAfter=Mar 4 13:56:53 2023 GMT
verify return:1
---
[...]
---
read R BLOCK
jN2kgmIXJ6fShzhT2avhotn4Zcka6tnt
Correct!
JQttfApK4SeyHwDlI9SXGR50qclOAil1
closed
Flag: JQttfApK4SeyHwDlI9SXGR50qclOAil1
Bandit Level 16 → 17
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
Solution
Proceed to scan port on localhost in range 31000-32000 first. of course, using the nmap
We can see the 31790 port running ssl service. Try connecting this port and see:
Great, that’s all we need. Copy it to clipboard and move on next Challenge!
Bandit Level 17 → 18
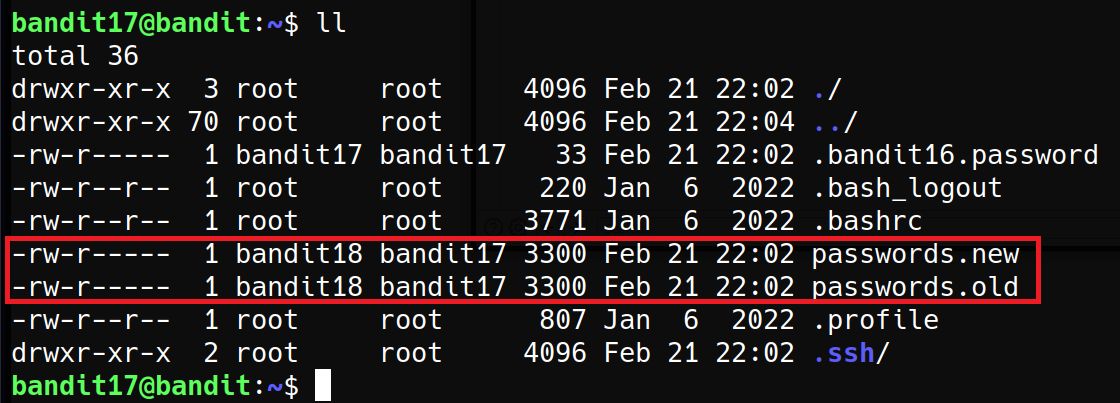
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
NOTE: if you have solved this level and see ‘Byebye!’ when trying to log into bandit18, this is related to the next level, bandit19
Solution
We use the private SSH key file to login in bandit17’s box
“It is required that your private key files are NOT accessible by others.” So I’ll modify the permission of it for only user to read it.
1
chmod 400 bandit17.private
Then try reconnect and it’s successful.
There are 2 files as mentioned in the description and we have to findout the only line that has been changed between them.
With the given hints, we just need to know about diff command usage.
Let’s proceed to diff two password files!
1
2
3
4
5
6
bandit17@bandit:~$ diff passwords.old passwords.new
42c42
< f9wS9ZUDvZoo3PooHgYuuWdawDFvGld2
---
> hga5tuuCLF6fFzUpnagiMN8ssu9LFrdg
Flag: hga5tuuCLF6fFzUpnagiMN8ssu9LFrdg
Bandit Level 18 → 19
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
Solution
Try connecting the bandit18’s box then immediately logged out. due to the modified .bashrc file.
1
2
3
Byebye !
Connection to bandit.labs.overthewire.org closed.
So I try using dash instead of bash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(dyl4n㉿kali)-[~]
└─$ ssh -t bandit18@bandit.labs.overthewire.org -p 2220 /bin/dash
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
bandit18@bandit.labs.overthewire.org's password:
$ ls
readme
Yep, it works. Let’s get the password in readme file and move on!
1
2
$ cat readme
awhqfNnAbc1naukrpqDYcF95h7HoMTrC
Flag: awhqfNnAbc1naukrpqDYcF95h7HoMTrC
Bandit Level 19 → 20
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
Solution
When logged in, we can see the highlighted file named “bandit20-do”. It seems like a binary file. 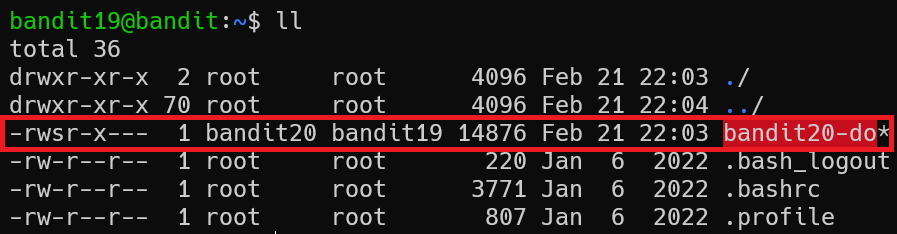
I proceed to execute it and then it displayed something like that
1
2
3
bandit19@bandit:~$ ./bandit20-do
Run a command as another user.
Example: ./bandit20-do id
Maybe it’s executable file and help me to be able to execute command under bandit20’s permission. No-doubt I run the file along with cat /etc/bandit_pass/bandit20 to get the flag!
1
2
bandit19@bandit:~$ ./bandit20-do cat /etc/bandit_pass/bandit20
VxCazJaVykI6W36BkBU0mJTCM8rR95XT
Flag: VxCazJaVykI6W36BkBU0mJTCM8rR95XT
Bandit Level 20 → 21
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
NOTE: Try connecting to your own network daemon to see if it works as you think
Solution
My idea is to create a listener and simultaneously send the previous level password (I use nc with pipe line). Then using suconnect file to connect that port and it’ll return my expect output.
1
2
bandit20@bandit:~$ echo -n "VxCazJaVykI6W36BkBU0mJTCM8rR95XT" | nc -lp 8888 &
[1] 2301973
The -n flag is to prevent newline characters in the input.
-lp: listener port
Then, we try using file ./suconnect to connect to that port and get the password!
1
2
3
4
bandit20@bandit:~$ ./suconnect 8888
Read: VxCazJaVykI6W36BkBU0mJTCM8rR95XT
Password matches, sending next password
NvEJF7oVjkddltPSrdKEFOllh9V1IBcq
Flag: NvEJF7oVjkddltPSrdKEFOllh9V1IBcq
Bandit Level 21 → 22
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Solution
Try seeing the content of cronjob_bandit22 at /etc/cron.d
1
2
3
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
As we can see, there’s a bash script at /usr/bin/cronjob_bandit22.sh and it execute something.
1
2
3
4
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
It seems like output of bandit22’s password file is redirected to /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv under the bandit22 user’s privilege. Let’s get password there!
1
2
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
WdDozAdTM2z9DiFEQ2mGlwngMfj4EZff
Flag: WdDozAdTM2z9DiFEQ2mGlwngMfj4EZff
Bandit Level 22 → 23
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
Solution
1
2
3
bandit22@bandit:~$ cat /etc/cron.d/cronjob_bandit23
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
Here’s the content of /usr/bin/cronjob_bandit23.sh. First, we need to understand this bash script.
1
2
3
4
5
6
7
8
9
bandit22@bandit:~$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
This script will do something like that: myname variable is the bandit’s user, mytarget is the md5hash and echo the password of bandit23 to /tmp/$mytarget as I mentioned
Here’s the flag!!
1
2
3
4
bandit22@bandit:~$ echo I am user bandit23 | md5sum | cut -d ' ' -f 1
8ca319486bfbbc3663ea0fbe81326349
bandit22@bandit:~$ cat /tmp/8ca319486bfbbc3663ea0fbe81326349
QYw0Y2aiA672PsMmh9puTQuhoz8SyR2G
Flag: QYw0Y2aiA672PsMmh9puTQuhoz8SyR2G
Bandit Level 23 → 24
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!
NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around…
Solution
Let’s see the bandit24 cronjob: 
It’s a piece of code. Let’s see how it works
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname/foo
echo "Executing and deleting all scripts in /var/spool/$myname/foo:"
for i in * .*;
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
owner="$(stat --format "%U" ./$i)"
if [ "${owner}" = "bandit23" ]; then
timeout -s 9 60 ./$i
fi
rm -f ./$i
fi
done
To put it simply, I will explain the overview.
First of all, this script will “Executing and deleting all scripts in /var/spool/$myname/foo:” with $myname is the current user. Instead of bandit23 user, I replace it with bandit24 in order to the script run Executing and deleting all scripts that I put in /var/spool/bandit24/foo/ . Based on that, I easily read the bandit24’s password.
Thence, I myself write a tiny script to handle above idea.
Create a temp folder and make it full permission. 
Write a small script to get the bandit24’s password. 
Before moving the scripts, Besure that the script’s executable 
Wait a minute,
Flag: VAfGXJ1PBSsPSnvsjI8p759leLZ9GGar
Bandit Level 24 → 25
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
You do not need to create new connections each time
Solution
To pass the challenge, we need enter the password for user bandit24 and the secret 4-digit pincode on a single line, separated by a space.
There’re 10000 combinations of 4-digit pincode, shell-script’ll help us in this case.
1
2
3
4
5
6
7
8
#!/bin/bash
pass=VAfGXJ1PBSsPSnvsjI8p759leLZ9GGar
for i in {0000..9999};
do
echo $pass' '$i;
done | nc localhost 30002
Go to /tmp and create a yourself directory, we work under it to run the shell script.
Flag: p7TaowMYrmu23Ol8hiZh9UvD0O9hpx8d
Bandit Level 25 → 26
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
Solution
There’s a private key file in bandit25’s home directory.
Lets try login as user bandit26 using this key with command:
1
ssh -i bandit26.sshkey bandit26@localhost -p 2220
We connect to localhost because bandit26 also exists the same server device as bandit25. 
Looking the output looks like we logged in bandit26 but logout immediately.
According to the level goal, “The shell for user bandit26 is not /bin/bash”. Lets findout what shell bandit26 is being used, shell’s information is in the ‘/etc/passwd’:
Let’s have a look at content of ‘/usr/bin/showtext’
The shell script using the ‘more’ command and the output is the contents of text.txt, after that exit immeadiately.
After researching ‘more’ for a while, I’ve gathered some cool stuff:
- More is a filter for paging through text one screenful at a time.
- If the amount of content to be displayed is larger than the terminal size, the more enable interactive mode.
- v’ Start up an editor at current line. The editor is taken from the environment variable VISUAL if defined, or EDITOR if VISUAL is not defined, or defaults to “vi” if neither VISUAL nor EDITOR is defined.
I try resizing the terminal window size smaller till the interactive mode is enabled
Yeah, now we can resize terminal windows bigger to handle easily
As I mentioned, we just hit v to convert to vi editor.
Vim has a mode called Command-Line Mode where you can enter your own commands in Vim. Googling to know how to use it :)
Flag: c7GvcKlw9mC7aUQaPx7nwFstuAIBw1o1
Bandit Level 26 → 27
Good job getting a shell! Now hurry and grab the password for bandit27!
Solution
Do the same steps as the previous level to login bandit26.
bandit27-do has suid bit, Try running it and see how it goes.
1
2
3
bandit26@bandit:~$ ./bandit27-do
Run a command as another user.
Example: ./bandit27-do id
Let’s get the password thanks to bandit27-do run command:
1
2
bandit26@bandit:~$ ./bandit27-do cat /etc/bandit_pass/bandit27
YnQpBuifNMas1hcUFk70ZmqkhUU2EuaS
Flag: YnQpBuifNMas1hcUFk70ZmqkhUU2EuaS
Bandit Level 27 → 28
There is a git repository at ssh://bandit27-git@localhost/home/bandit27-git/repo. The password for the user bandit27-git is the same as for the user bandit27.
Clone the repository and find the password for the next level.
Solution
Run the following command to clone the git repo (remember to create a folder in /tmp to work on):
1
git clone ssh://bandit27-git@localhost:2220/home/bandit27-git/repo
Enter password as the bandit27’s password that we can clone this repo.
After clone it, go to /repo and read README file to get password.
Flag: AVanL161y9rsbcJIsFHuw35rjaOM19nR
Bandit Level 28 → 29
There is a git repository at ssh://bandit28-git@localhost/home/bandit28-git/repo. The password for the user bandit28-git is the same as for the user bandit28.
Clone the repository and find the password for the next level.
Solution
Same as the previous challenge, let’s connect and clone repo to your own temp directory.
1
ssh://bandit28-git@localhost:2220/home/bandit28-git/repo
There’s a README.md file in the repo.
No password here but it mentions ‘bandit29’. Try reviewing some recent commit by using git log.
add missing data sounds interesting. Let’s see the changes of file in this commit using git show
1
it show 6c3c5e485cc531e5d52c321587ce1103833ab7c3
Flag: tQKvmcwNYcFS6vmPHIUSI3ShmsrQZK8S
Bandit Level 29 → 30
There is a git repository at ssh://bandit29-git@localhost/home/bandit29-git/repo. The password for the user bandit29-git is the same as for the user bandit29.
Clone the repository and find the password for the next level.
Solution
clone repo to your own temp directory and check README.md file.
1
git clone ssh://bandit29-git@localhost:2220/home/bandit29-git/repo
Maybe there is a development branch exisiting in the repository. Check existing branches:
Let’s checkout remotes/origin/dev and re-check the README.md file
1
2
3
4
5
6
7
8
bandit29@bandit:/tmp/tmp.G0EVhgUlAE/repo$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: xbhV3HpNGlTIdnjUrdAlPzc2L6y9EOnS
Flag: xbhV3HpNGlTIdnjUrdAlPzc2L6y9EOnS